There’s a hacker attack every 39 seconds around the world!
Sounds scary? Well, the truth is, if you are on the Internet today, your data is vulnerable to cyber-attacks. (Unless you take some strong security measures.)
Online security has become an issue of prime importance in today’s scenario. But do you know how to protect yourself from cyber threats?
The answer is simple – Enable 2FA on your accounts!
This article is about the Best 2FA Apps, where I’ll be covering everything about Two Factor Authentication – what it is, why it is important for us, popular authentication methods, and major 2FA Factors for selecting a good authenticator app.
Later, we will also discuss what authenticator apps are, how to set them up in 4 easy steps, and discover the 9 Best 2FA Apps for 2024!
For this review, I have personally tested and researched all the featured apps for an entire month, after which I am here with the in-depth review!
For best security always combine password manager with a 2 FA App. If you really wish to know how to enhance your online security, do read this article till the end!
Now, with no more delay, let’s find out the 9 Top 2 Factor Authentication for Android & iPhone
- What is 2FA?
- Why should you use 2FA?
- What are 2FA Factors?
- Common types of 2FA
- What is MFA?
- TOTP vs HOTP
- What is an Authenticator App?
- How to use a 2FA App?
- What are the Factors for Selecting the Right Authenticator App?
- Best 2FA Apps
- Conclusion
- FAQ
What is 2FA?
Two Factor Authentication (2FA) is a method to verify the users’ identity. It adds a second layer of security to our online accounts and helps websites ensure we are indeed who we are claiming to be!
Let’s understand this with an example. If you wish to sign in to your Facebook account, what do you need?
- Your email id/username
- Your password
This is Single Step Verification because by typing in the correct credentials, we are logged in with no questions asked!
But do you know how this process can be risky? Literally anyone can have your Email ID. And, if your password is not powerful enough, hackers can certainly attack your account! (If it’s “123456”, you’re in trouble, friend!)
Therefore, 2FA was introduced. Now, even if someone has your email and your password, they can still not get into your accounts.
2FA introduces a second step of verification where you need to provide a set of information that only you, the authentic user, can possess.
This prevents unauthorized users from gaining access to your sensitive information. Today, many popular websites and services support 2FA to ensure safer logins.
Why should you use 2FA?
As I mentioned above, implementing 2FA doubles your online security. Let me tell you the 4 major reasons why you need to use 2FA right now on all your important accounts.
1.Data Breaches
Hackers have become smarter than ever, and our online information is constantly at risk!
Where millions of emails and passwords are leaked and sold out on the dark web every other day, 2FA provides us a secure way to take back control of our accounts.
2. Weak Passwords
Well, who doesn’t love convenience? When asked for setting up a password on our Instagram, what have we all got? Our pet’s name, our mobile number, birth date, and whatnot!
The problem is that all these passwords are easy to guess for anyone, and can be cracked within minutes!
You keeping these as passwords is like inviting hackers to come and take away your account! 😛
3. Reused Passwords
We all have so many accounts on the Internet these days that it’s a headache to remember unique passwords for them all, right?
So, we end up using the same passwords on multiple accounts. But do you realize the major flaw here?
If a hacker gets access to one of your accounts, they might try the same password on all your other accounts, and oh your privacy would be compromised in a matter of minutes!
This is also why you should use a password manager to create complex and unique passwords for every account.
4. Common Security Questions
Many websites (for example Namecheap, Upwork, etc) let you add security questions as the second step of verification of your account. So, every time you log in, you’re presented with questions ranging from your mother’s maiden name to the name of your first school or your first pet!
If someone has access to your personal information through different online accounts like your social media, he/she can easily guess the answers to these questions.
2FA can protect you in all of these situations by requesting for a second factor for authentication.
Wondering how? Let’s find out!
What are 2FA Factors?
If you enable the 2FA function for securely logging in to your accounts, you would also need to provide a second factor along with your credentials. It might be any of the following!
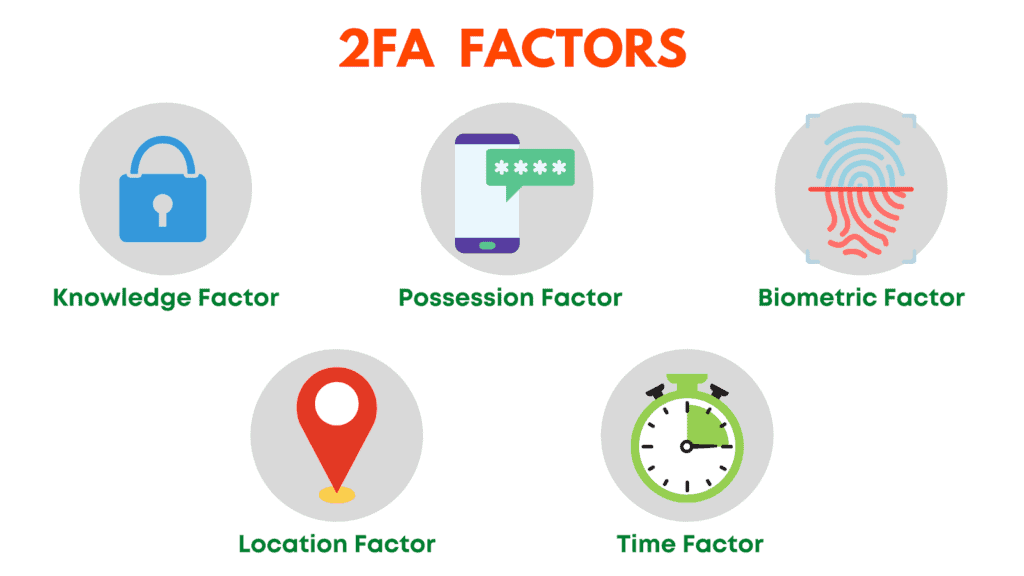
1. Knowledge Factor
It is a memory-based factor that comprises something you know or remember. For example, PIN, Password, Security Questions, etc.
2. Possession Factor
It involves providing something you have. For example, hardware tokens, codes through a TOTP authenticator app, SMS codes, Email codes, etc.
3. Biometric Factor
This requests you to provide something that you are. For example, your fingerprint, face scan, retina, voice, etc.
4. Location Factor
This type of authentication lets users login only from certain approved locations.
5. Time Factor
Time Factor accepts logins only during a specific time range. You cannot log in outside of that time slot.
So, these are different factors for performing a two factor authentication. It’s not mandatory to secure all your accounts, and not all sites give you the option to do so either!
But important sites and apps that hold your sensitive data, for example, social media accounts, password managers, banking or finance related accounts containing your confidential information should definitely have 2FA enabled!
Common types of 2FA
Now, let us look at the common 2FA implemented by popular websites and apps these days.
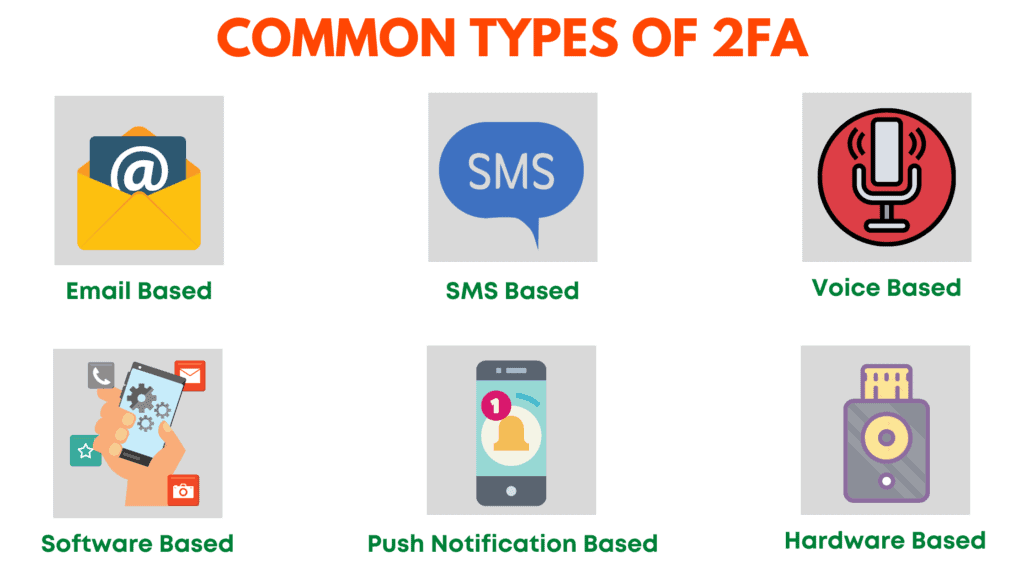
1. Email-based 2FA
Email-based 2FA requires you to enter verification codes sent to your email id. Most websites use this type of verification when you login from a new device.
However, it is the least secure because hackers can get hold of your email account by simply performing a Brute Force Attack!
You should avoid Email-based verification whenever possible, and go with the other kinds of 2FA discussed below.
2. SMS-based 2FA
This is a fairly common type of authentication which requires you to enter the verification code sent as an SMS on your mobile number.
However, it is believed to be an unsafe option because hackers can easily intercept text messages by hacking your mobile operator.
3. Voice-based 2FA
In Voice-based 2FA, they deliver your passcode to you through a voice call on your mobile or landline phones. Again, this option is not extremely secure because phone calls can be tapped too.
4. Software token/TOTP based 2FA
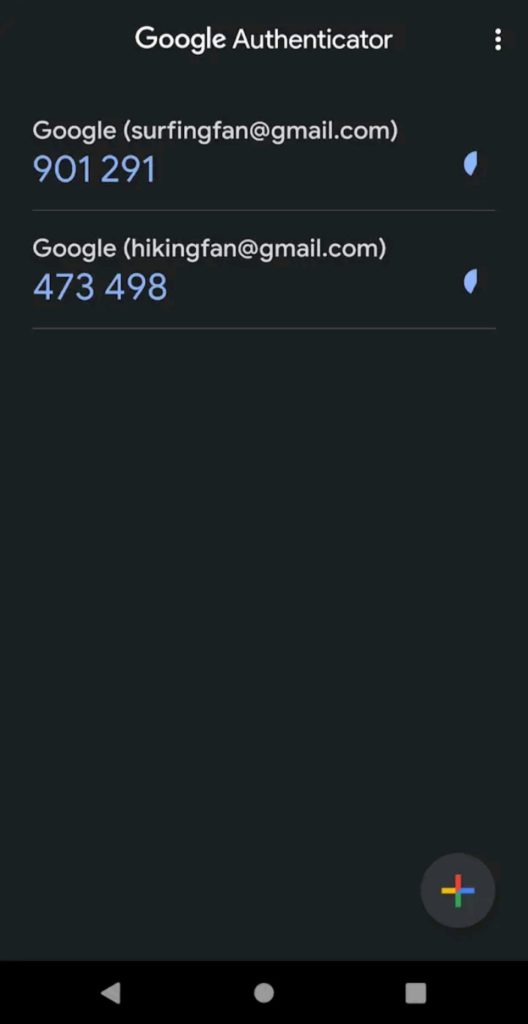
In TOTP-based authentication, a software called an Authentication App installed on your mobile/desktop generates dynamic 6-digit login codes.
These codes are used to login to your accounts. Because they only remain active for around 30-45 seconds, this method is quite secure.
Some examples might be Twilio Authy, Google Authenticator, etc.
5. Biometrics based 2FA
Biometrics-based 2FA converts the user itself into a token! Here, you are asked to provide your fingerprint, face ID, voice, or retina scan to validate your identity.
6. Push Notification based 2FA
This is a more secure form of 2FA. Whenever a login attempt is made on your account, you receive a push notification on your trusted devices about the login attempt along with its location, device type, and browser used.
You can choose to accept or deny the request, which makes it super helpful in preventing unauthorized access.
Cryptocurrency companies, online money transfer services, and finance related companies use it to ensure better security.
7. Hardware Token-based 2FA
This type of 2FA uses a hardware device that generates a unique 6-digit code every 30-60 seconds.
The device looks like a keychain and you can carry it around with ease. It is by far the most secure form of 2FA. For example, Yubikey.
What is MFA?
Multi factor Authentication (MFA) is one of the most secure methods of authentication. It makes use of two or more of the above mentioned ways to validate your identity.
Basically, websites that support MFA implement two or more authentication steps to every login, reducing the chances of a cyber-attack dramatically!
Popular services including Facebook, AWS, Apple, Microsoft, GitHub, etc support Multi-factor Authentication.
Here’s a simple example to help you understand it.
Let’s say I enable MFA on my Facebook account. Now, after entering my username and password, it might ask me to provide a security PIN.
After confirming this step, it might ask me to enter the authentication code through an app which is only available in a 30-second window!
So, this is how MFA minimizes any possible risks and threats to your accounts.
TOTP vs HOTP
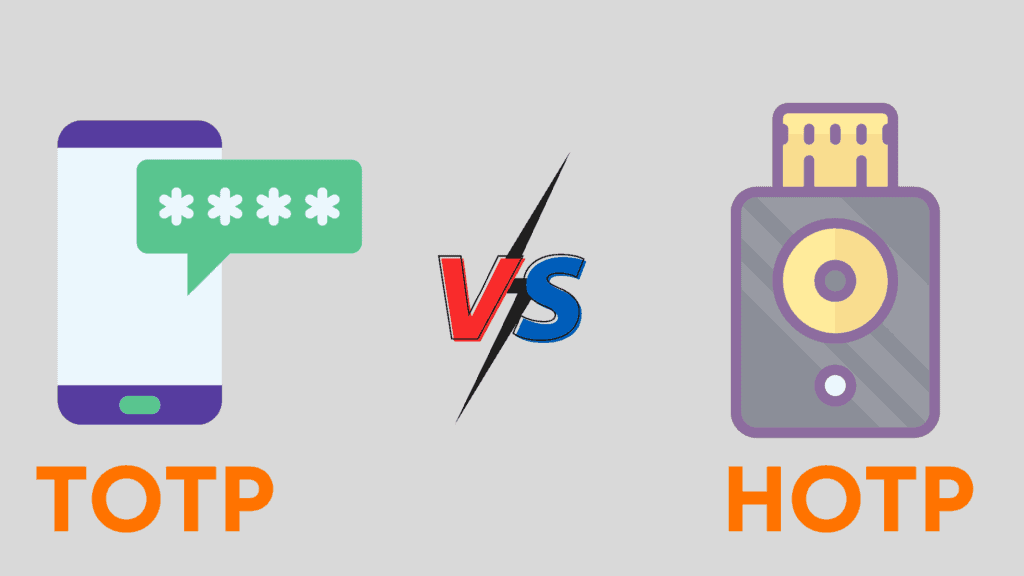
TOTP stands for Time-based One-Time Passwords. These codes are time-based, which means they remain active for 30 to 60 seconds. If not used within that time period, they become invalid.
Some examples of TOTP apps might be Authy, Google Authenticator, etc.
On the other hand, HOTP stands for HMAC-based One-Time Passwords. These codes are event-based, which means they remain active till the user requests a new code.
An example might be Yubiko’s Yubikey.
What is an Authenticator App?
An Authenticator App is a software that generates unique security codes to ensure secure logins to your online accounts.
These codes keep changing every 30 seconds, which is why the chances of your account getting hacked are minimized!
You can install authenticator apps on your desktop or mobile devices. They do not require an Internet connection in order to generate codes.
They are also lightweight and handy. So you can simply install them, set them up, and start using them instantly!
How to use a 2FA App?
It’s pretty easy to get started with an Authenticator application, which I’ll prove to you in a minute. All popular 2FA apps almost work the same way.
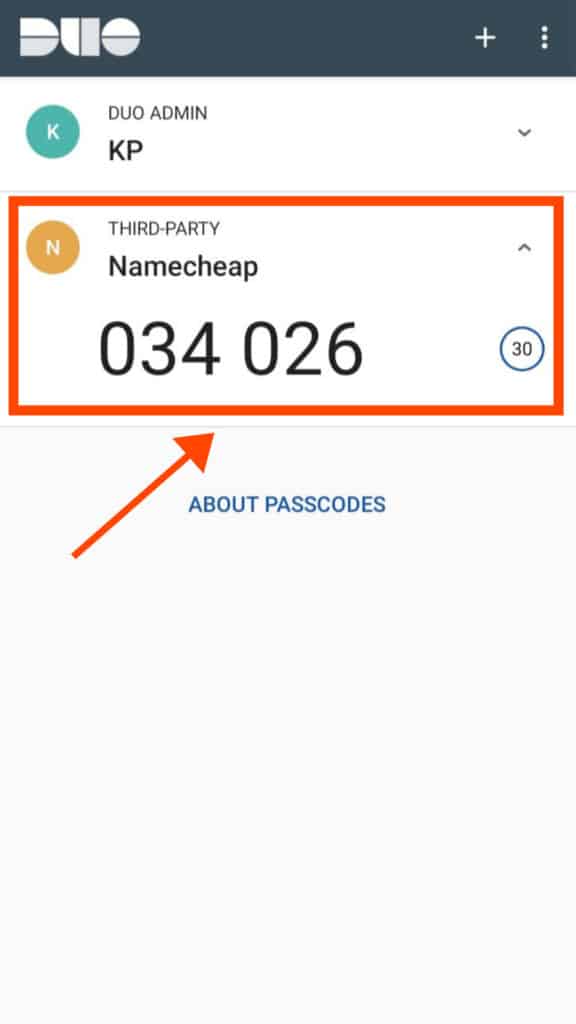
For the demonstration, I have taken the Duo Mobile app to enable 2FA on my Namecheap account.
Following these simple steps, you can activate 2FA on any of your online accounts that support this service.
Step 1
We will install the Duo Mobile app on your mobile. This app also needs an account to be created first.
Step 2
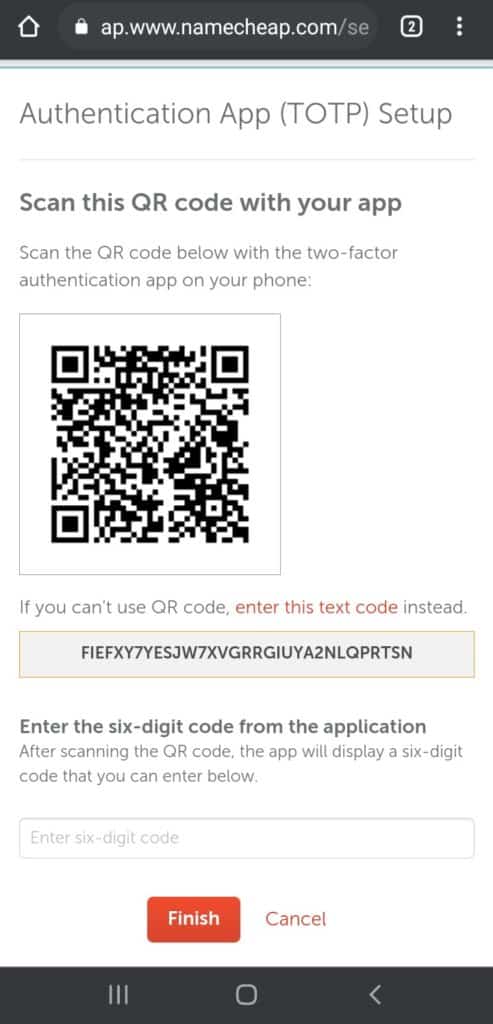
Now, we will head over to the security settings on our Namecheap account and click on Enable 2FA.
The website will display a secret text code or a QR code to scan through your Authenticator app.
Step 3
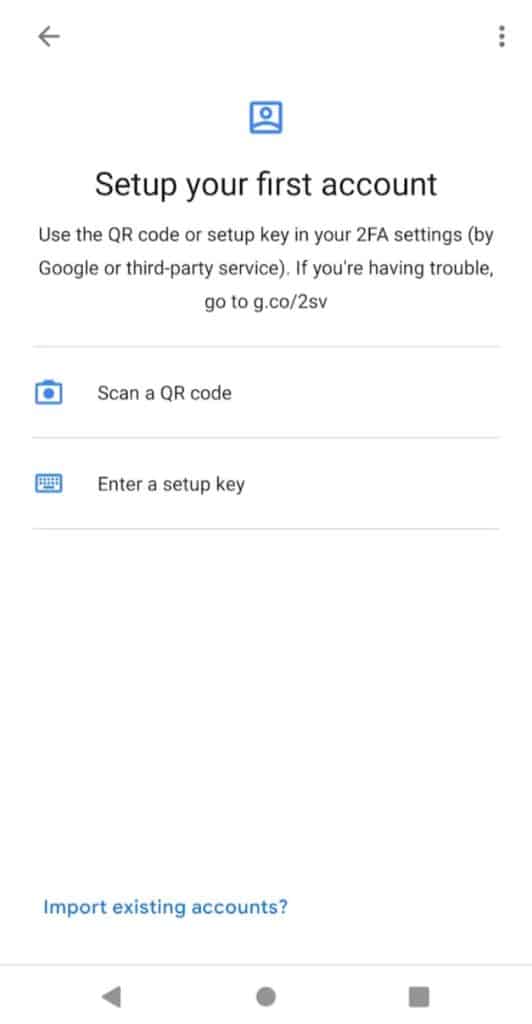
We will click on the + button in our 2FA app.
We can either scan the QR code visible on the website or enter the secret code.
Step 4
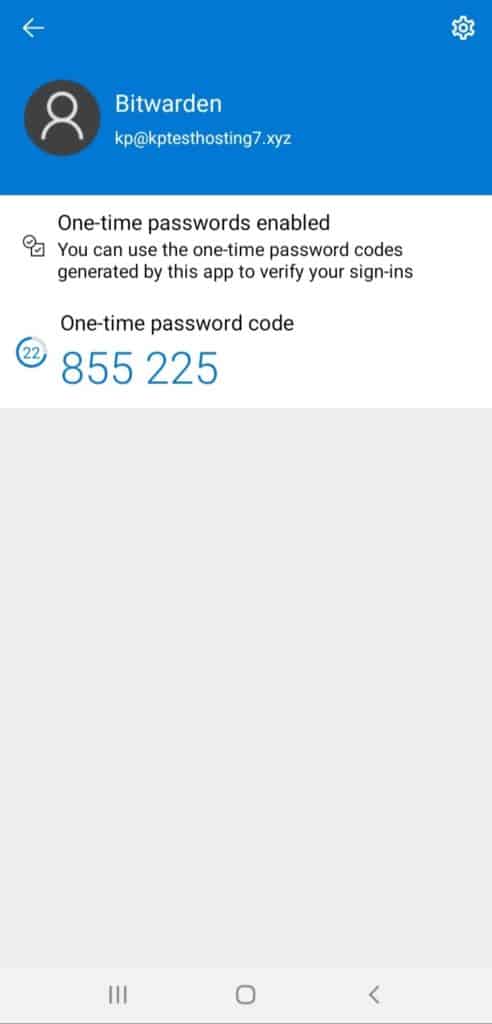
Finally, we would be asked to enter a code generated by the app for verification.
Within seconds, the 2FA service would be enabled on our Namecheap account and we can use it to secure our further logins.
Some websites also provide backup codes while setting up 2FA. You can use these codes to log in when you have trouble with your TOTP codes.
What are the Factors for Selecting the Right Authenticator App?
Now that you know what an Authenticator app is and how it functions, let us see how to select the correct app for you.
I have used the following factors to analyse the Best 2FA apps for this article!
1. Pricing
2FA is a simple enough process to ensure your online security. So, a good authenticator must let you access its functions for free.
We do have an exception in our list below. To know more, keep reading further.
2. Offline Access
All the popular authenticator apps are lightweight and do not require an internet connection in order to generate codes.
So, even when you need to sign in to one of your accounts and your mobile has no internet, your OTP codes would work the same.
3. Open Source
A good authenticator app should be open source so its source code is available for anyone to see.
This also helps researchers and developers find bugs and issues in the code and resolve them as soon as possible!
4. Passcode Protection
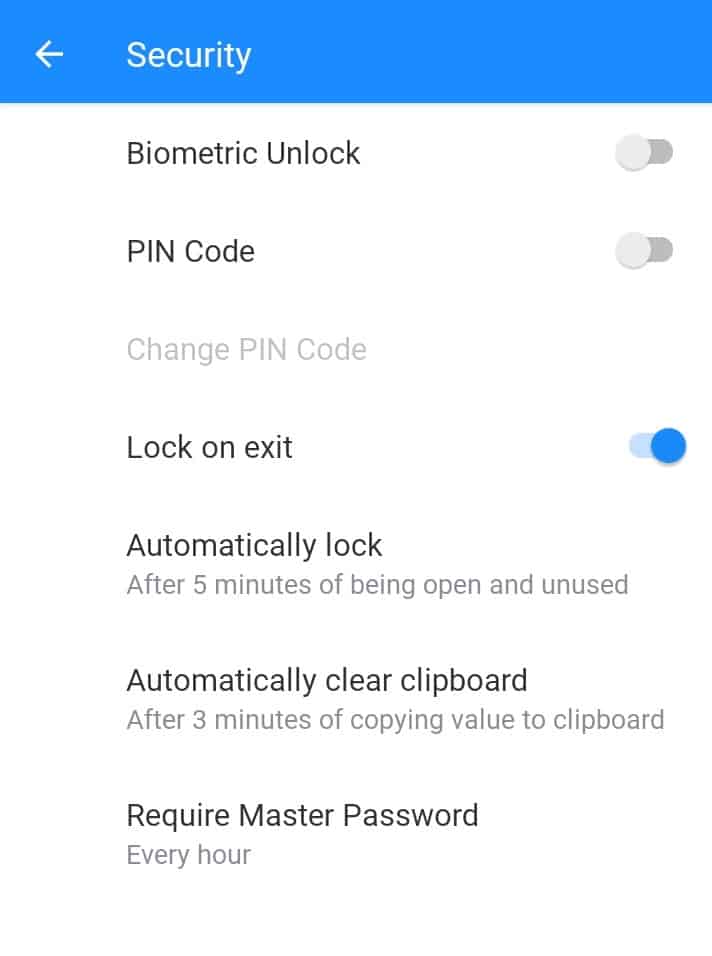
An authenticator app is meant to protect your security. It should comprise options to lock the app with a PIN, a passcode, or even better, your biometrics like fingerprint, face id, etc!
5. Biometric Lock
Biometric Lock lets you access the authenticator app with your fingerprint or face ID.
This is great if you don’t want to get into the hassle of remembering one more password!
6. Backup and Restore
An authenticator app must allow you to create secure backups of your security codes and also restore them with ease whenever you want.
7. Autofill and Autologin
Using this feature, your authenticator app can automatically fill the OTP code and log you in to your account. You don’t need to do anything at all.
However, this function is rarely provided by authenticator apps. Again, we have exceptions in our list! Stay tuned!
8. Import Entries
This is useful when you want to switch to a new authenticator. Always check if the app offers any options to import your previous entries.
This would save up a lot of your time setting everything up from scratch again.
Also check if there is direct support of other authenticators, or if you can upload CSV files, etc.
9. Export Entries
Similarly, in case you wish to switch to a different authenticator, always confirm for suitable export options.
Verify what formats you can export the files in, and if they are supported by other apps.
10. User Interface
There’s nothing specific about the interface. The app should be easy to set up, use and access. All the functions should be easily available.
11. Alteration of Code
Some apps also let you change the time interval for which an OTP remains active. The maximum limit, however, is 60 seconds.
Similarly, some apps allow you to vary the OTP code’s length. So instead of 6 characters, you can change it to 8 characters, making your logins even more secure!
12. Desktop App
If your authenticator also has a desktop app, you don’t even need to have your mobile phone around for getting your codes.
You can simply log in through your desktop/laptop and the process would become way more smooth, time saving, and effortless!
13. Multi-Device Sync
A good authenticator app should let you sync your entries across all the devices you use – be it laptop, mobile, or a PC. You should be able to access your OTP codes quickly with no troubles.
14. Password Manager
This is an extra feature which is not necessarily required. Most of the popular 2FA apps are dedicated authenticator apps.
However, Microsoft, 1Password, etc provide you inbuilt password manager functionality. So, you can save your login credentials along with your secret codes all at the same place.
15. Dark Mode
Though, this might not be the most important factor, having a dark mode definitely adds to the user’s experience.
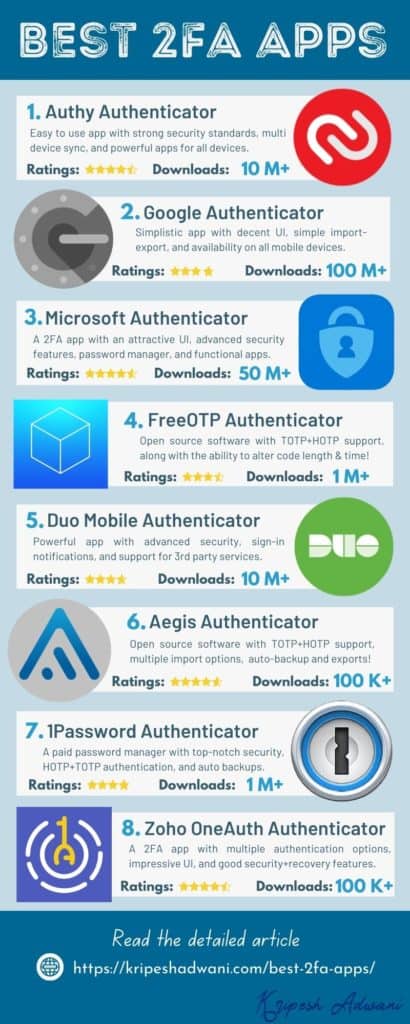
9 Best Two-Factor (2FA) Authentication Apps For 2024
1. Authy
The biggest competitor of Google Authenticator is here! Authy is a powerful and flexible authentication software developed by Twilio, a Cloud Communications Company based in San Francisco.
Not only is it a user-friendly and elegantly designed authenticator app, it is also available for anyone to use for FREE!
Let us check out what Authy app offers.
Features
Easy to Set Up
Setting up Authy on your mobile is super easy. Download the app, sign up using your phone number, get your identity verified either through a call or an SMS code, and you’re done!
Now, you can save your security codes inside Authy.
Encrypted Backups
The primary issue that we all face while using authenticator apps is that of losing our data. Fortunately, with Authy, you don’t need to worry about ever losing your codes!
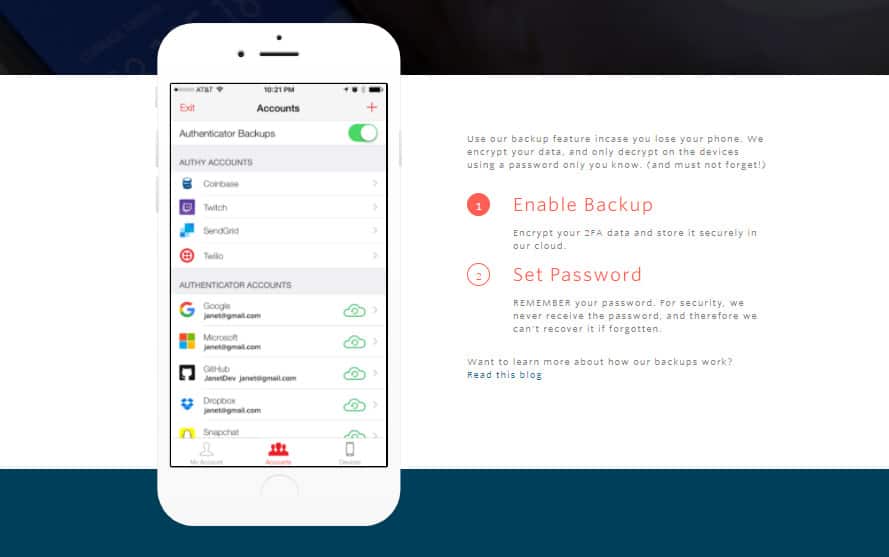
Not only does it allow you to create a backup of your OTP codes, but also stores them in an encrypted format protected through a password, so that nobody can access it except for you.
In case you lose your mobile, all you need to do is enter your mobile number and get your vault back!
Authy uses the SHA2 Algorithm and 256-bit encryption keys to save your data, so your security codes are 100% protected.
Offline Access
Authy does not require an Internet connection to function. It can generate OTPs offline. This makes it more easily accessible and reliable.
Powerful Security Lock
Authy lets you set a PIN or fingerprint lock to add an extra layer of safety to your accounts.

So, if any unauthorized person gets hold of your mobile, they can’t just access your 2FA codes without entering your 4-digit secret PIN or your fingerprint! Cool, right?
I liked how Authy intuitively switches to a numeric keyboard while asking for the security PIN. It really helps save time!
Great User Interface
Authy has a super simple and clean interface. You can switch between list and grid mode for easy accessibility of your OTPs. There’s a copy button beside the entries to copy your codes.
What I liked about Authy was its easy identification of websites. If I save 2FA codes for my Facebook account, Authy will display the Facebook icon beside the entry.
And if you switch to the grid mode, it displays OTPs for different saved accounts in full screen view. An expiry countdown runs below the code, which is extremely user friendly and convenient!
It also allows you to edit logos and names of the entries. And finally, it also has a dark mode to allow users to access it with ease 24×7!
Apps for All Devices
Authy has designed easy-to-use apps for all devices, be it your mobile or your desktop. These apps are also frequently updated.
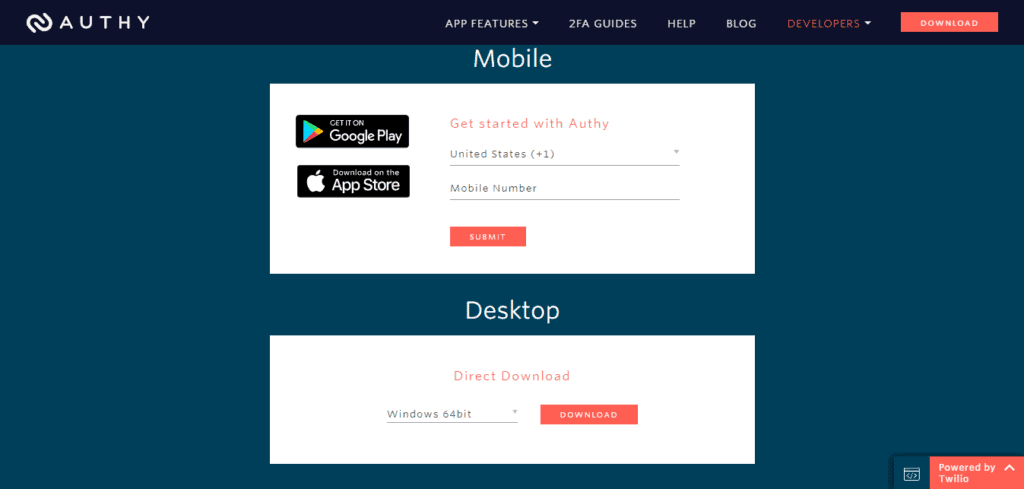
It offers powerful desktop apps for Windows, Mac, and Linux operating systems., compact mobile apps for Android and iOS devices and even offers a handy Chrome Extension to work from your browser!
Multi-device Sync
With Authy, your vault goes wherever you go! If you need to access the same services through multiple devices, then you would appreciate the sync feature.
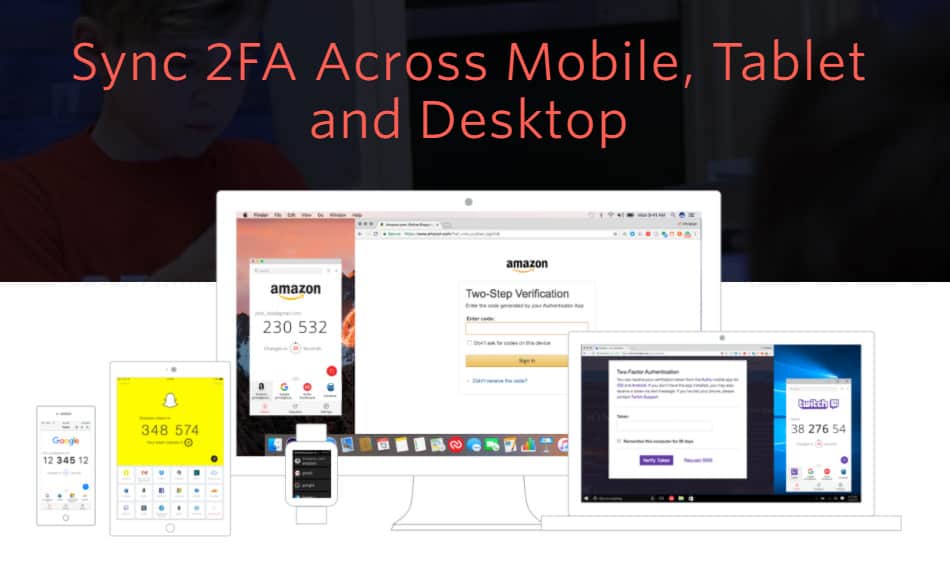
If you’re on a mobile device, get your codes on your mobile app. If you’re working from your desktop, simply get them on the desktop app or your Chrome extension! Every code can be accessed anywhere and anytime.
Disadvantages
Closed Source
This is the only con of Authy. Its source code is not available for anyone to see, which is why its security and privacy cannot be trusted!
Conclusion
So, Authy is an intuitive app jam packed with impressive features for security, encrypted backups, and syncing on multiple devices.
If only it were open-source, Authy would’ve been unbeatable in the market right now!
2. Google Authenticator
Google Authenticator is the most popular Authentication app in the online world right now! Google developed it for implementing two-step verification for its users.
Millions of people are using Google Authenticator, all thanks to its simplicity and ease of use.
Though Google Authenticator app is well-designed, and supports all major websites, it lacks some significant features. Let us look at it in detail.
Features
Easy to Set Up
Oh, you seriously don’t need to do anything at all! Just download the app, and you are ready to go.
Scan QR codes from your favourite services and secure your logins instantly.
Simple Import and Export Functions
With Google Authenticator, you can export your account from an old device and import it into your new device with a single click!
Simply click on the Export button and it will create a QR code for your entire vault. As soon as you scan it on a new device, you can import all your data. I think this is an impressive feature!
Decent User Interface
The interface of Google Authenticator is simple and clean. However, I found it a bit boring! There are no icons displayed beside the website which makes it difficult for the user to find the required login.
The code can be copied by holding your thumb over the OTP on your mobile. It also has a dark mode which works as an added advantage.
Access on Mobile Devices
The Google Authenticator app is available for free download on an iOS, Blackberry, and Android phone, which basically means you can use it on all the mobile devices!
However, they can work on developing a desktop app or a browser extension to make it more widely usable!
Check Suspicious Activities
Google authenticator lets you keep a tab on the recent activities of your account under the Transfer Accounts tab. This is an excellent feature to monitor suspicious login attempts, etc.
Enter your Setup Key
In case you cannot scan the QR code, Google Authenticator also lets you enter the secret key provided by the website. But make sure to select ‘Time based’ in the key type to receive TOTP codes.
Time Correction for Codes
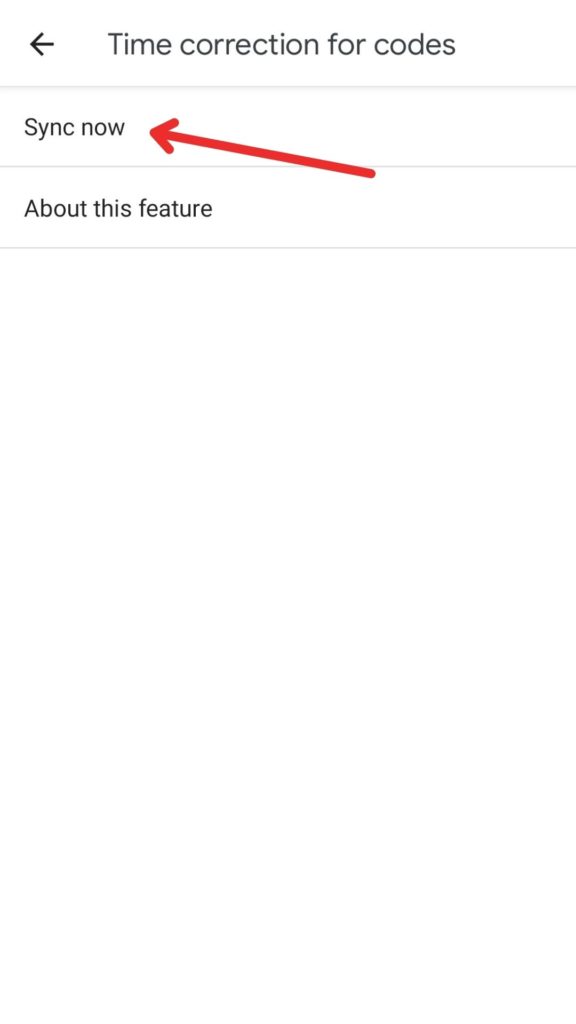
In case you cannot receive OTPs or your codes are not working, Google Authenticator has a time correction feature as well. It quickly syncs the time in your app and all your codes start working perfectly again.
Disadvantages
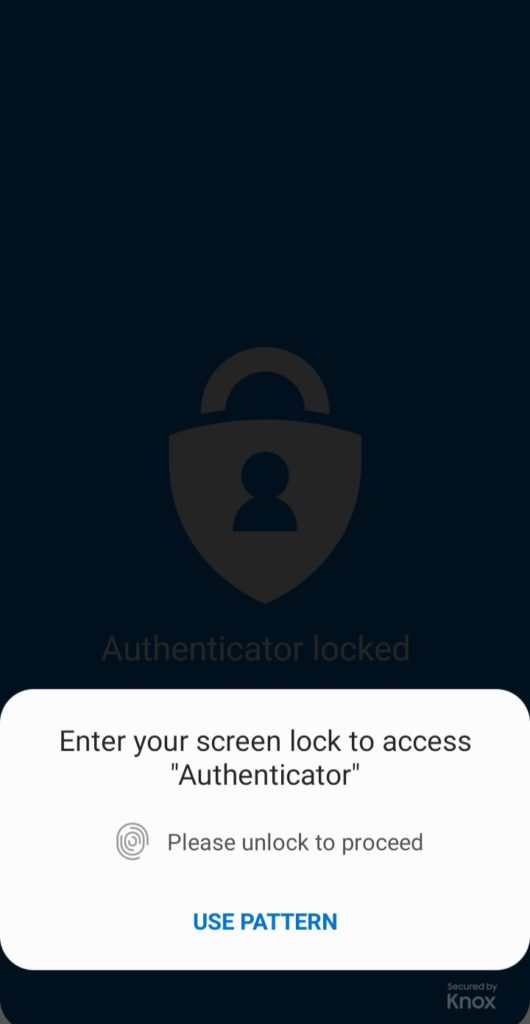
Lack of Security Features
Google Authenticator disappointed me on this point. The app does not offer any security functions like a Pin/Password/Biometric Lock to protect our logins.
This raises major concerns on your privacy because anyone getting hold of your mobile phone can also get all your 2FA codes and take over your accounts in no time!
You wouldn’t want that, would you?
No Backups
Though you can import and export your vaults into a new device, there’s no backup feature! So, in case you did not export your entries into a new device and lose your current device or even delete the app, there’s no way to get your vault back!
No Sync Functions
Because you can use it only on one device at a time, there’s no way to sync your entries.
Though you can export your account on multiple devices to access it from different mobiles, every newly added entry needs to be updated again, which is an inconvenient and time-consuming process.
Conclusion
Google Authenticator is your easy-to-use software available on all mobile devices.
But the lack of major functions like security lock, backup, and sync makes it a less viable option than Authy or Microsoft Authenticator.
3. Microsoft Authenticator
Microsoft Authenticator is the official two factor authentication app put forward by Microsoft.
It has a free version you can use to securely sign in to your online accounts. That said, let’s delve into its important features!
Features
Powerful Apps
Microsoft Authenticator is available as a sleek mobile app for Android, iOS, and Windows 10 mobiles, and as a Desktop app for Windows OS. I found its apps to be decent. They also receive updates frequently.
Good Security Features
It offers a biometric/PIN based lock for every time you enter the app. This ensures an additional security of your OTP codes.
It also sends security notifications to your app in case your account is signed in from a new location or a new device, or your password is changed, etc.
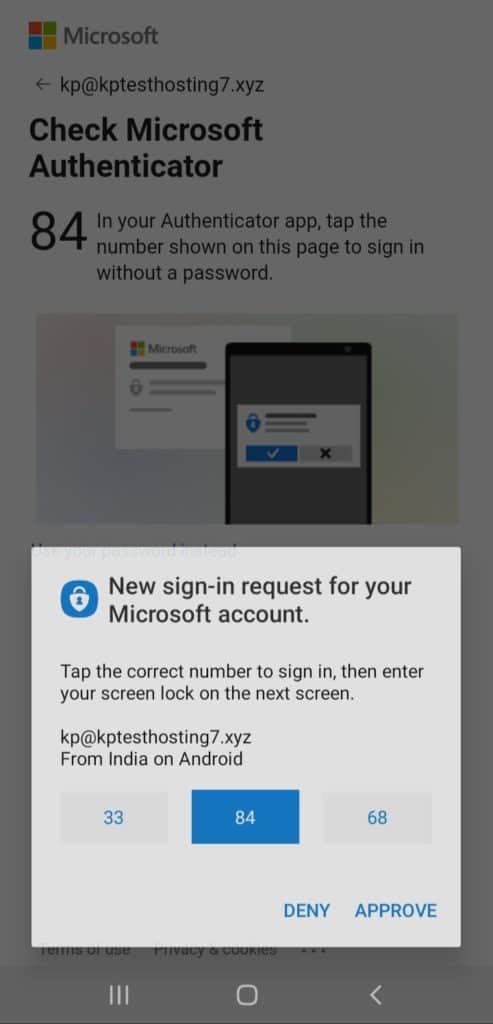
Passwordless Sign-In
By signing in with a Microsoft account, you can enable a passwordless sign in for Microsoft services.
For example, if I try to login to my Microsoft account from my desktop, I’ll receive an approval notification on my mobile app, asking me to accept or deny the login request.
This is a great security measure to only approve authorized users.
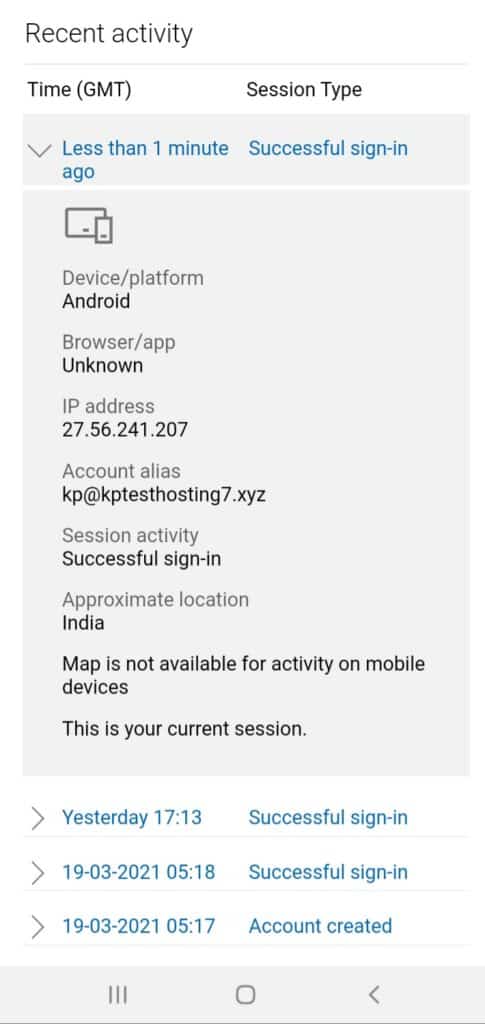
Review Recent Activity
Microsoft Authenticator app also lets you review any recent activities on your account.
This helps keep a tab on suspicious activities around your accounts.
Decent Interface
The user interface of Microsoft Authenticator is decent. It shows website icons beside the OTP entries, which is great! To copy a code, you just need to click on it! The Dark Mode option seems to be missing here!
What I liked about it is the ‘Hide codes’ option that requires you to tap on a particular entry to reveal the code. This is great from the security point!
Microsoft Password Manager
The most interesting thing about Microsoft Authenticator is an in-built password manager that you can enable by signing in through your Microsoft account.
This makes it easier to manage your entries and login into your accounts.
Whenever you go to a website, the password manager would autofill your credentials, and the authenticator would autofill the OTPs, eliminating any efforts from your side!
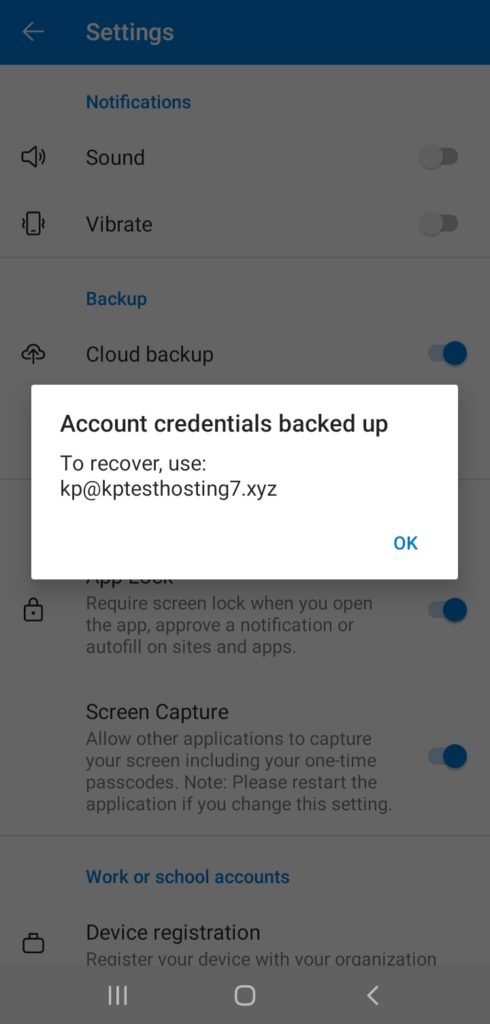
Good Backup and Restore Options
If you sign in through your Microsoft account, it also allows you to enable the Cloud backup.
So, if you’re using an Android device, your data always remains safely stored on Microsoft’s servers and you can restore it anytime you want! It also supports iCloud Backup for iPhone users.
AutoFill Function
For an authenticator app, this is an advanced function. Microsoft Authenticator automatically fills in your passwords and your 2FA codes.
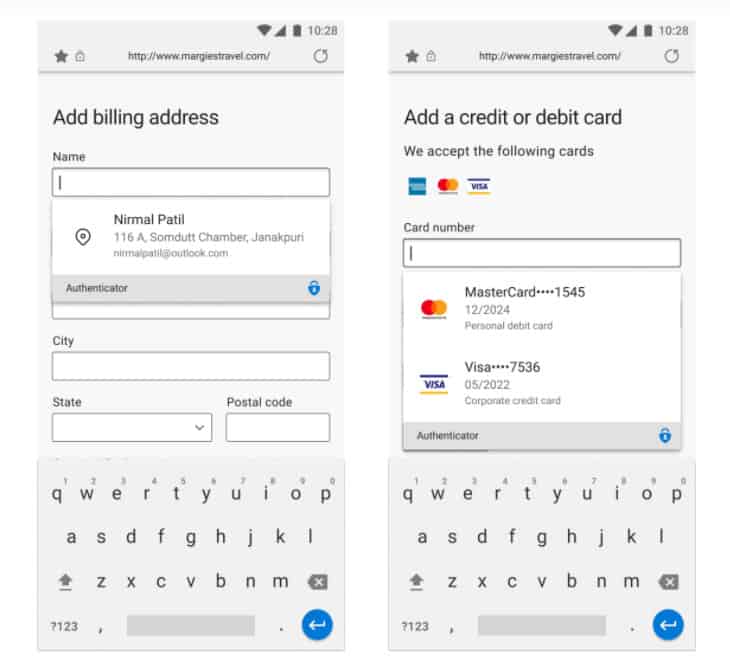
As per a recent update in October 2022, it now supports autofilling addresses and payment details as well. All you need to do is set Microsoft Authenticator as your default autofill provider.
While autofilling payment details, it verifies the user’s biometrics to confirm they are the real owner of the device. This adds another layer of security to autofilling your sensitive details.
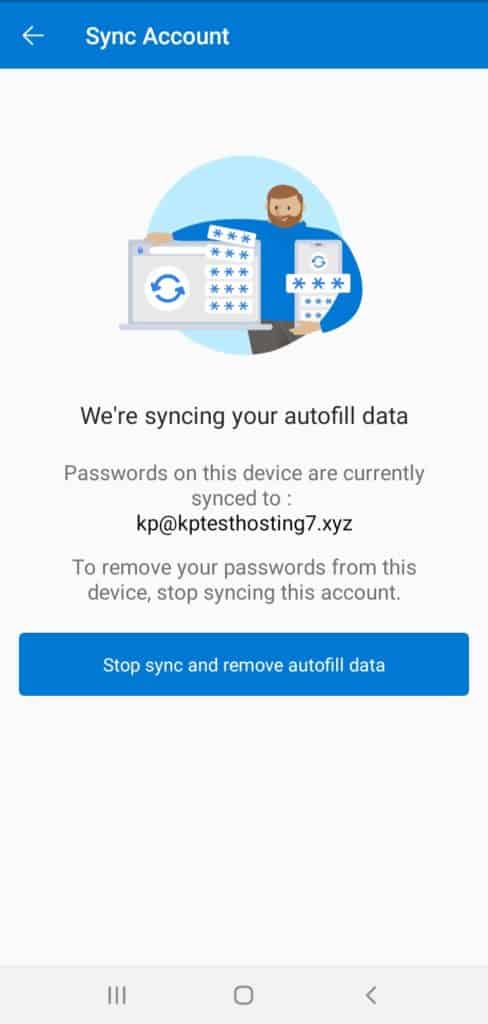
Multi-Device Sync
The sync function syncs all your passwords and OTPs to your Microsoft account, so you can access them on any other device.
You can also stop syncing and remove the autofill data through a single click!
Device Registration
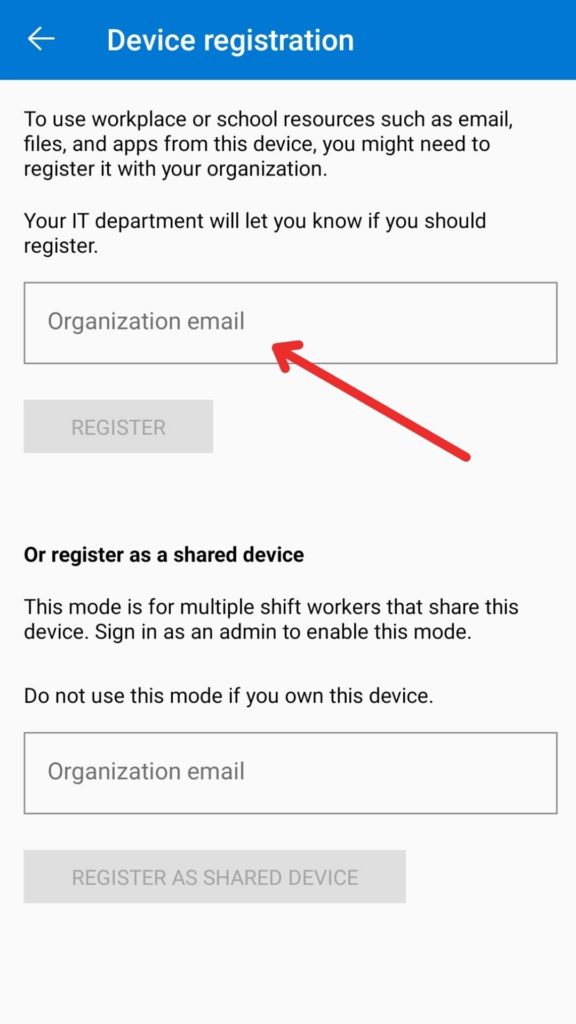
If you wish to use the files and apps from your workplace, Microsoft Authenticator also offers an option to register your device. This way, you can access your school’s or organizations resources easily on your device.
Disadvantages
No Direct Export Options Available
You get the Cloud Backup option. But there’s no option to download the backup of your data. I feel they should have provided that option as well.
Some Functions Require Internet Access
Some features like Backup, reviewing activity on our Microsoft account, accepting or denying login requests, etc require access to the Internet, which takes away the convenience factor.
Limited Support
Microsoft Authenticator is best for people who use Microsoft services heavily.
Many users have reported that it doesn’t support a lot of common applications, but works well for Microsoft services.
Conclusion
Microsoft Authenticator is a feature-rich solution for implementing 2FA. It offers all important functions including backups, security, a friendly interface, multi-device sync, and more!
Though it supports many services, you can use it if you heavily use Microsoft services. It works perfectly with them.
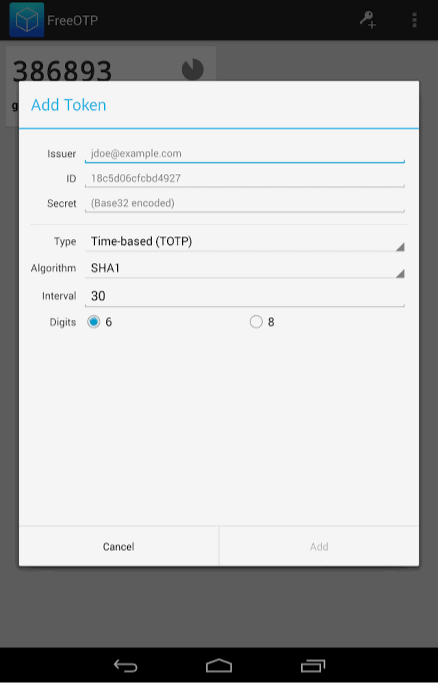
4. FreeOTP
FreeOTP is an open source and completely free 2FA software developed by RedHat. It is available for Android and iOS devices. Let us look at its features in detail.
Features
Free and Open Source
FreeOTP, as the name suggests, is a free software that is also open-source. This means its source code is available for anyone to access.
This helps security experts and researchers identify bugs and issues in the code and resolve them swiftly! Along with that, it also works offline.
Decent UI
The interface of FreeOTP is decent, but looks a little old. Icons are displayed for popular websites and services, which is good.
What I liked about it is that you can copy the codes by clicking on them. And the codes are not visible directly on the screen.
They are hidden behind hyphens. So you need to click on them to view them, which is good for security.
Supports TOTPs and HOTPs
FreeOTP supports both software and hardware based authentication. So you can easily add Yubikey or other hardware keys as a 2FA.
Alter Code Length and Time
This is a rare feature that I did not expect to find in FreeOTP. If you manually enter a security key for any service, you can select the length of your OTP code (6 or 8 digits), and the time interval for which it remains active.
You can also choose the hashing algorithm with which your codes will be secured. And for hardware based 2FA, a counter can also be entered.
Disadvantages
No App Security
Sadly, FreeOTP does not offer any security features like PIN, Passcode or Biometrics unlock to secure your codes. This might be risky because anyone can access the OTP codes to your confidential accounts!
Infrequent Updates
The FreeOTP Android app is outdated and has not received any updates since 2016!
No Backups and Sync
FreeOTP is a basic authenticator app with very basic functions. First, it does not provide any import or export functions. Second, you won’t find any backup or restore functionality either.
And finally, it does not allow you to sync your data on multiple devices, which makes FreeOTP a less viable option to use!
Conclusion
The best thing about FreeOTP is that it’s open-source. Other than supporting both software and hardware based 2FA, and letting you customize the code lengths, it’s a very basic app.
It lacks app security features, backup and sync functions, a good interface, and frequent updates.
I don’t feel it’s safe to use an app that hasn’t been updated in the last 5 years. What do you think? Let me know in the comments section below.
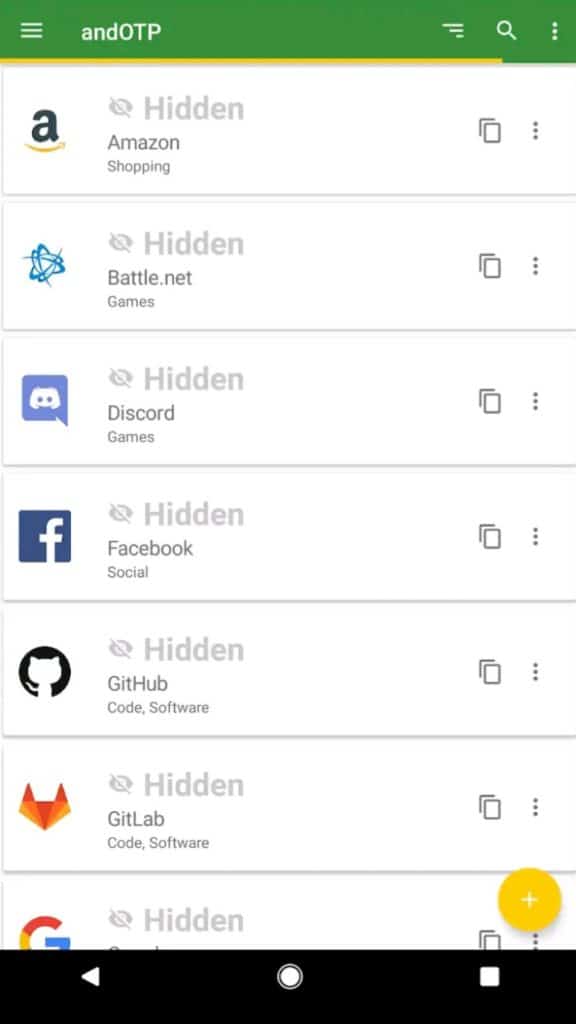
5. andOTP
andOTP is a very new authentication software developed by Jakob Nixdorf in October 2020. It is a free and open source software, which is why it is gaining popularity in the market right now!
Let’s check out what it has got for us!
UPDATE: As of April 2022, the andOTP Authenticator has been removed from Playstore because of an error encountered in its review process. In case you still wish to use this 2FA app, you can find the andOTP APK on Github.
Features
Decent User Interface
I liked the interface of andOTP app. It is neat and easy to use for a new user.
It supports icons for different websites and you can even customise the icons as per your choice!
I can copy OTPs through a copy button beside the code. It also offers a dark mode which is very convenient for better use during the night!
You also get to see lots of options for adjusting the font size, thumbnail size, customizing the tap functions, etc.
Free and Open Source
This 2FA software is completely free and open-source. Because its code is available for the general people, it is a bit more trustworthy!
If interested, you can check out the source code of andOTP on GitHub.
It doesn’t require an Internet connection to work, which is great!
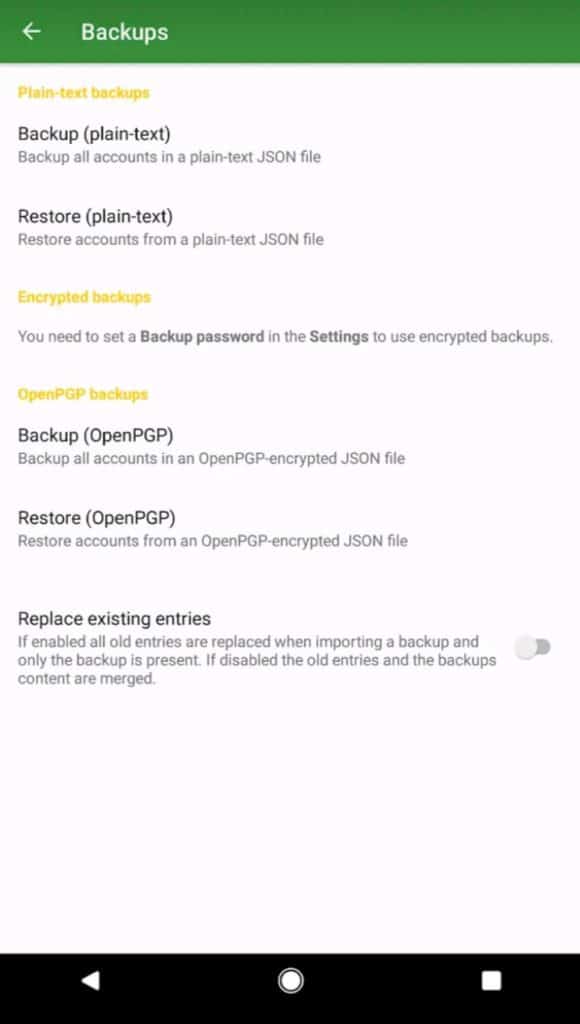
Multiple Backup and Restore Options
andOTP offers a variety of Backup options. You can either backup and restore your accounts in plain text, or encrypted formats, which is an advantage from the security point!
You can also enable OpenPGP backups, for which you would need to install an OpenPGP provider.
Your encrypted backup can be password protected to add another layer of security!
Another very interesting and convenient feature is that you can choose to either replace existing entries or merge them with the new ones after restoring a backup.
Supports TOTP and HOTP methods
This app supports both software and hardware based 2FA, which means you can login through OTP codes and use hardware devices like Yubikey to authenticate your logins.
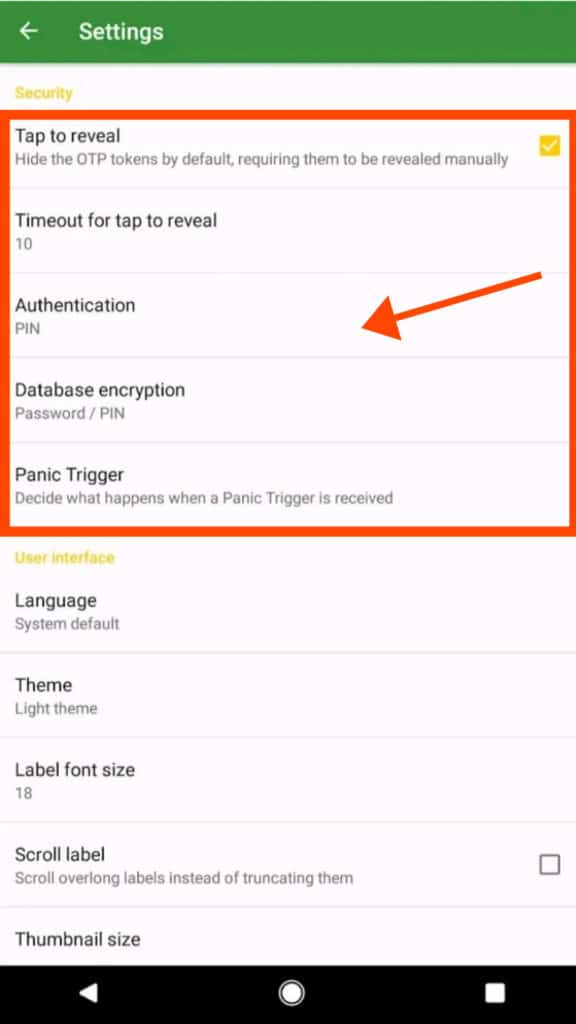
Tap to Reveal Function
This feature lets you set a time (between 5 sec to 60 sec), after which the OTPs are automatically hidden. I think it’s a good security function!
Database Encryption
Before using andOTP, it requires you to choose one of these methods to encrypt your database:
- Password lock
- PIN lock
- Android Keystore
Whatever method you choose would be required every time you need to access the app. There are no options to disable this encryption, which is great for security!
You will find some handy features for customizing when you want to re-lock the app!
Panic Trigger
Panic Trigger is a unique and secure feature. It lets you either wipe out all your saved accounts or reset the app settings in case of emergency situations!
Disadvantages
Only supports Android OS
A major disadvantage of andOTP is that it only supports Android devices.
However, with this limited support, it offers support for all versions of Android, including rooted devices.
No Import and Sync Functions
andOTP does not allow you to import entries from other 2FA apps or file formats. Absence of sync features is also a downside!
Conclusion
Being an open source solution, andOTP is loaded with premium features like mandatory database encryption, a variety of backup options, and Panic Trigger for emergencies!
The only flaw is that you can only use it on Android devices. I think they should advance their support to iOS devices too.
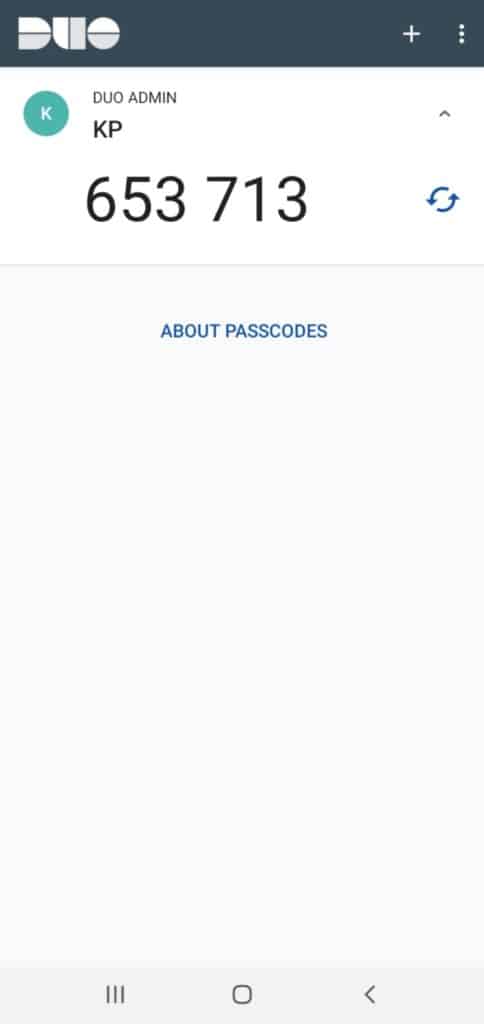
6. Duo Mobile
Duo Mobile is an authenticator application developed by Duo Security, a company focussed on creating secure MFA options for the users.
In 2018, Cisco acquired Duo Security. So, Duo Mobile can be called a Cisco product now.
Though this application is primarily designed for enterprises for multi-user authentication, you can easily use their free plan for personal authentication!
Now, let us look at its features one by one!
Features
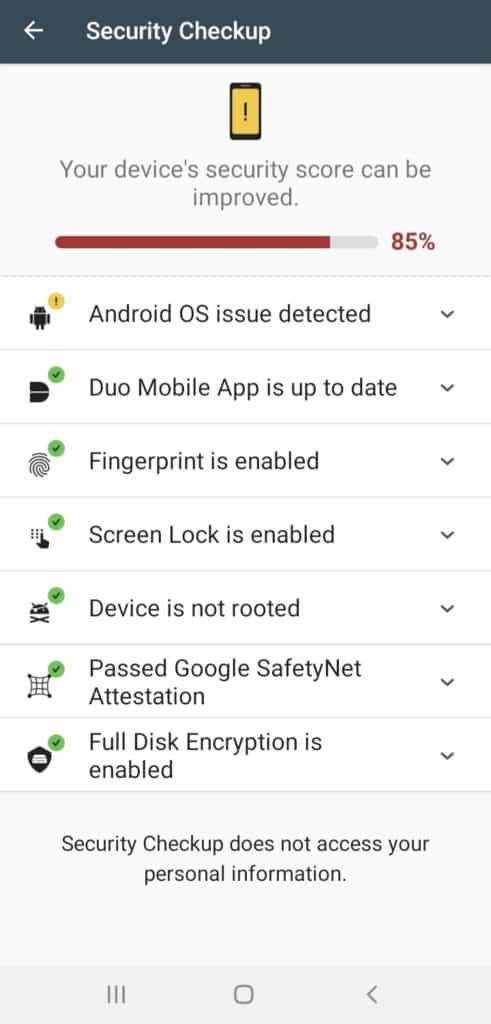
Security Checkup
The Security Checkup feature analyses and rates you in terms of security measures taken.
It verifies if you have enabled the screen lock and biometrics, if your device is running the latest OS and the latest version of Duo Mobile App, etc.
I think this function is very helpful as a reminder to regularly update our security.
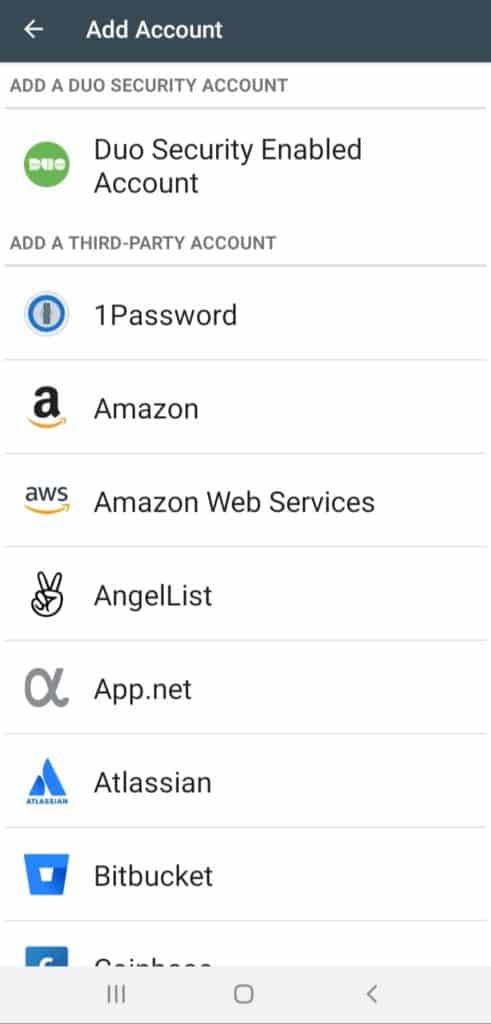
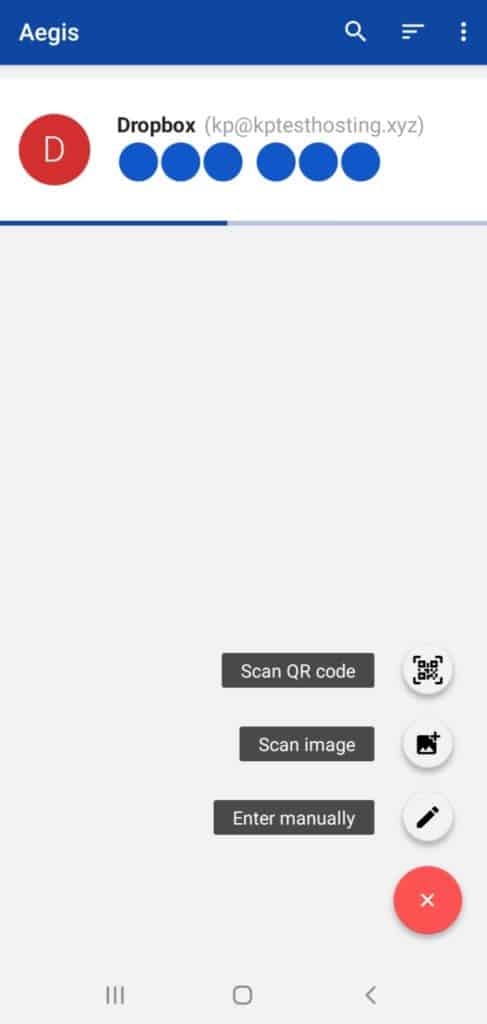
Supports Third Party Services
Besides other services, Duo Mobile also supports 45 third party services including Facebook, Instagram, Dropbox, 1Password, Amazon, and more.
What I loved about Duo Mobile is that it offers support for a majority of websites and social media platforms, and its apps are frequently updated.
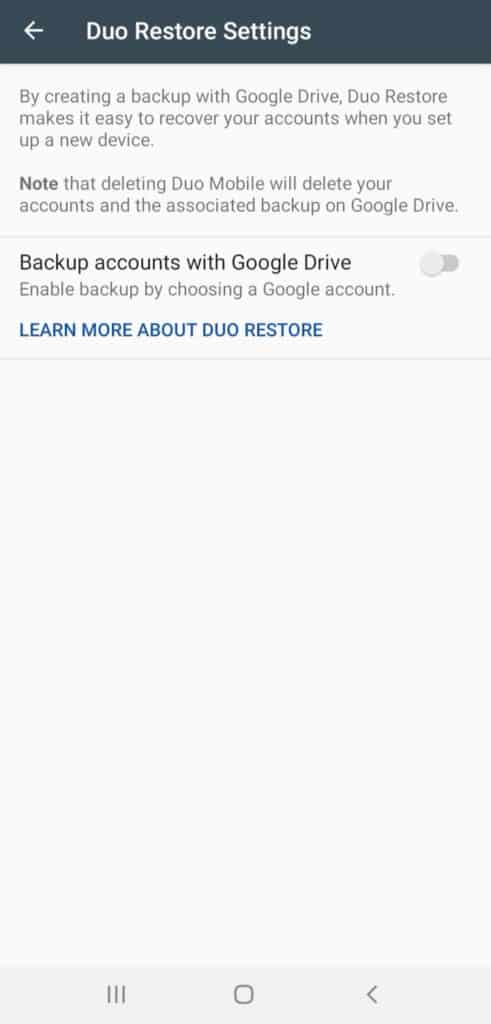
Encrypted Backups
You can back up all your accounts in an encrypted format using Duo Mobile.
For Android users, the backups can be stored on Google Drive, and for iOS devices, iCloud can be connected.
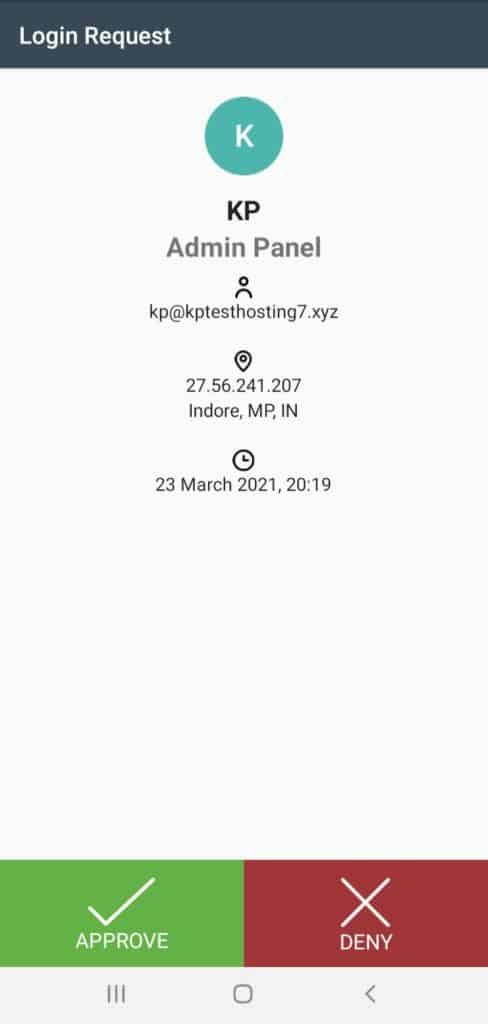
Push Notifications
This is the best feature of Duo Mobile! Every time you sign in to your Duo account from a different device, you receive an approval request on your app.
But that’s not all! It also shows you the date, time, IP address, and location where the login attempt was made from.
This is extremely helpful for preventing unauthorized users from accessing your accounts.
Disadvantages
No Offline Access
Duo Mobile is an online service. It requires an active Internet connection at all times to function, which proves as an inconvenience for most people.
Average UI
The user interface is not very impressive. It doesn’t assign icons to externally added accounts other than the 3rd party services.
Also, it doesn’t even mention the website name beside the 2FA codes. It just displays the username which might be the same for multiple accounts. This creates a lot of confusion while logging in!
What I liked about the interface is that the OTPs are hidden under the drop-down menu and you can copy them by simply holding on to the codes.
Conclusion
Duo Mobile is great for enterprises that need to authenticate multiple users. I found its Security Checkup and Push Notification features quite impressive. However, it only works with an active Internet connection.
7. Aegis
Aegis is a free and open source software for two factor authentication.
It is designed by Beem Development, which includes two software developers. Their aim was to create a secure 2FA app with some advanced functions that other 2FA apps lack!
Let’s check out what Aegis offers.
Features
Free and Open Source
Aegis is a totally free and open-source software, which means it is more secure. You can check the source code of Aegis on GitHub.
All its features work perfectly without an Internet connection!
Good Security Features
I liked the security features offered by Aegis. It lets you secure the app with PIN, password, or a fingerprint lock.
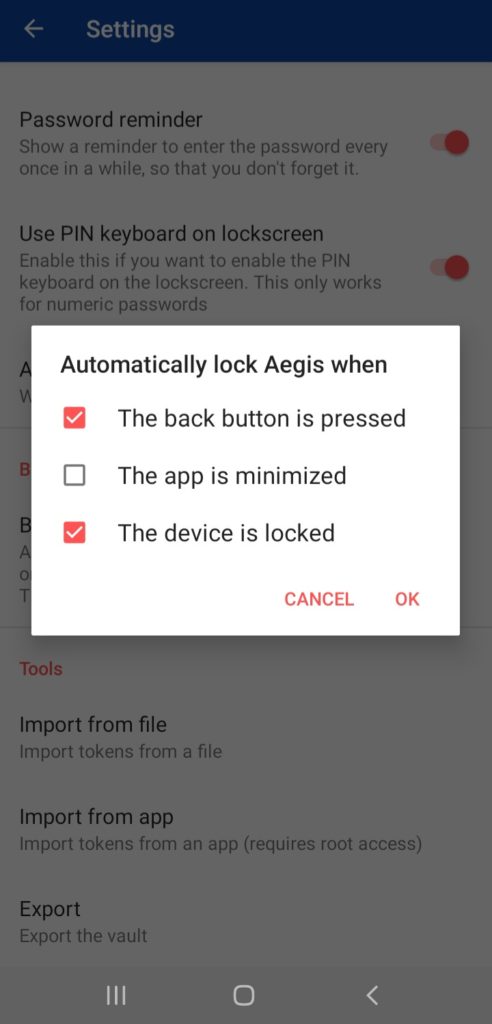
It has a Tap to Reveal function that hides the code until we tap on it.
You can select a time interval (between 5 to 60 seconds) after which the OTPs get hidden again.
Additionally, you can also enable auto lock for different conditions.
Supports HOTP and TOTP methods
Aegis supports both software and hardware based 2FA, which means you can even use hardware keys like Yubikey for authentication.
Lots of Import Options
It supports direct imports from popular apps including Authy, Google Authenticator, Microsoft Authenticator, FreeOTP, and even plain text files.
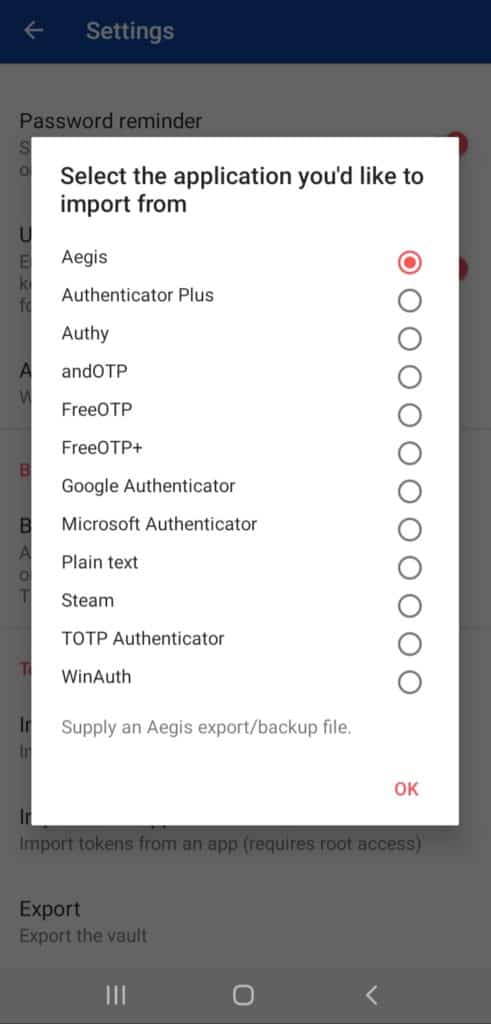
This is beneficial for users and saves up a chunk of time!
Good Interface
The interface is simple, clean, and decent. It also lets you import icon packs and select from three themes- Light, Dark, and Amoled. The users can select one according to their preferences.
However, there are no icons displayed beside the entries, even for popular websites.
For copying a code, you need to hold the code till a copy button appears above it. Don’t you think this is quite time-consuming for entering a code only available for 30 seconds?
Aegis offers three different view modes for changing the layout style of the vault. Clicking the Lock button locks your account with a single click.
And you can even enable the PIN keyboard for easy entry of passwords while logging in.
Auto-backup and Export
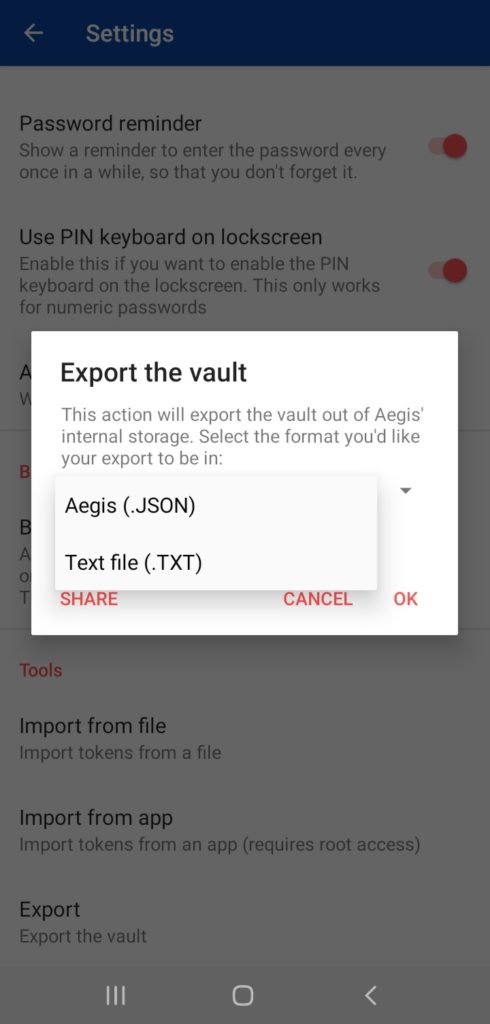
Automatic Backups can be created on the external storage.
And you can also export your entries to a new device in JSON or TXT formats.
Can Alter Code Length and Time
Another mind blowing feature that is rarely seen in authenticator apps is the ability to alter the code length and time for which it remains active.
Aegis allows you to enter a time and length for your OTPs and even lets you choose a hashing algorithm to keep your entries as secure as you want!
Panic Trigger
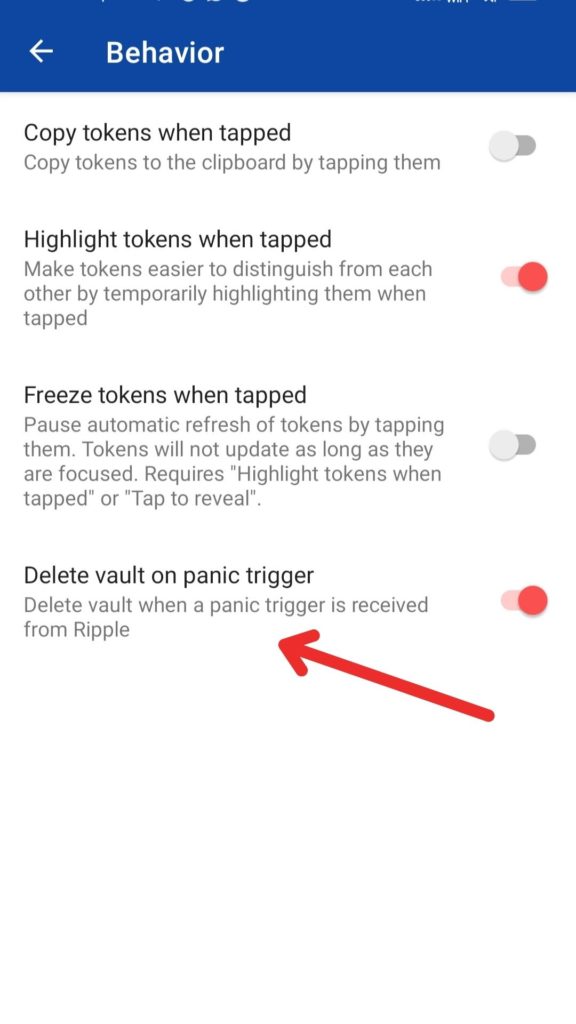
This is an interesting security features that would automatically delete your Aegis vault in case of emergency situations. You can enable or disable it as per your convenience.
Disadvantages
No Sync Features
Though you can export your entries and use them on multiple devices, I could not find any multi-device sync features on Aegis.
Conclusion
Aegis might lag behind in providing ease of access, but it offers some advanced functions to make up for that!
An open source software with significant security features and auto backup options, along with the ability to alter the TOTP code length and time – I think that’s a powerful package!
8. 1Password Authenticator
1Password is one of the most popular Password Managers developed by AgileBits in 2006. They also offer an inbuilt 2FA authenticator function, which is called the 1Password Authenticator.
Let us look at what features it offers!
Features
Powerful Apps for Desktop and Mobile
1Password has powerful, complete, and smooth working apps for all devices. This includes
- Desktop apps for Windows, Linux, and Mac
- Mobile apps for iOS and Android OS.
It even has browser extensions for popular web browsers.
Auto-Backups
Because the 2FA function is available under the 1Password app, you get to enjoy all the advantages of a password manager.
All your entries are automatically backed up on your device, and if you choose to connect a cloud service like Google Drive or iCloud, you can do that as well.
Great interface
The interface of 1Password is excellent! It is clean, and has a modern design.
You also get to see a Dark mode which is pretty convenient.
Supports both HOTP and TOTP based 2FA
Along with software 2FA, 1Password also supports hardware based authentication like Yubikey, which is great.
Autofill Entries
Unlike other 2FA apps, you won’t find the entries listed in the 1Password app.
But when you save your credentials for a website and also enable 2FA, you will be able to access the codes within the password entries. Or it also offers an auto-fill function for more ease of use!
Password Manager
Because 1Password is a password manager application, you can save all your website credentials along with your TOTP codes too, and easily access them anywhere and on any device.
Good Security Features
1Password lets you create a strong master password at the time of signing up for an account.
You can also enable a biometric lock feature with your mobile device.
Multi Device Sync
You can keep all your entries synced on multiple devices, be it your laptop, desktop, tablet or your mobile phone!
Disadvantages
Paid Service
Because 1Password is a paid software, the 1Password Authenticator also comes as a paid service. However, you can get a 14-days free trial of their services.
No Offline Access
As 1Password is a cloud based software, you need to remain connected to the Internet in order to use its 2FA functionality.
Conclusion
With 1Password, you get access to powerful features for security, backups, and sync, along with one of the best password managers!
However, this service is not free. So, check out my detailed 1Password Review article for understanding all its functions before purchasing this tool.
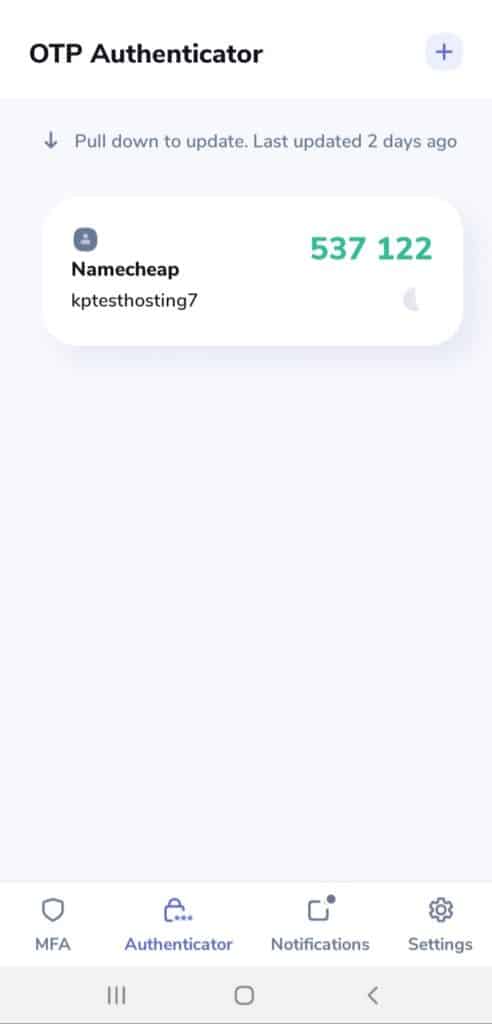
9. Zoho OneAuth
Zoho OneAuth is a Multi-factor authentication app by Zoho, an Indian company that develops software products, business tools, and cloud computing services. It looks like a promising product, so let us quickly dive into the details!
Features
Excellent User Interface
I loved the interface of Zoho OneAuth. It has a very attractive design and looks modern and elegant! It even offers a dark mode for better experience.
In order to copy a code, all you need to do is tap on it. This is quick and preferable.
However, what I did not like is that the OTPs are visible on the app screen, and there are no options to hide them.
Impressive Security Features
Under the ‘View Account Activity’ tab, you can keep a track of the recent activities on your Zoho account.
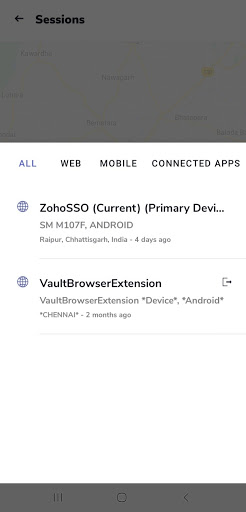
You can check the devices logged in to your account under ‘Active Sessions’.
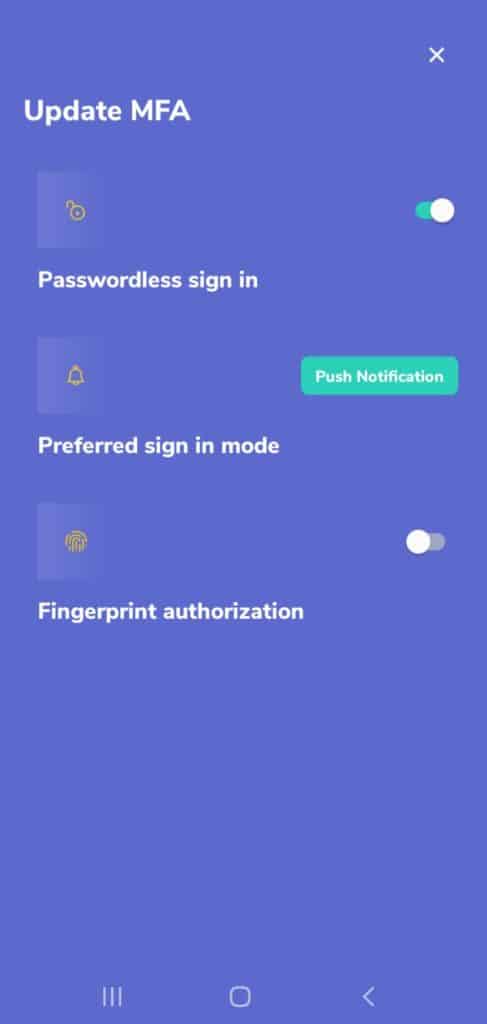
Multiple Authentication Options
Zoho OneAuth offers you multiple authentication options, so you can choose from any of the following:
- Fingerprint or Face ID
- Push Notifications
- QR code
- Time based OTP
Push Notifications
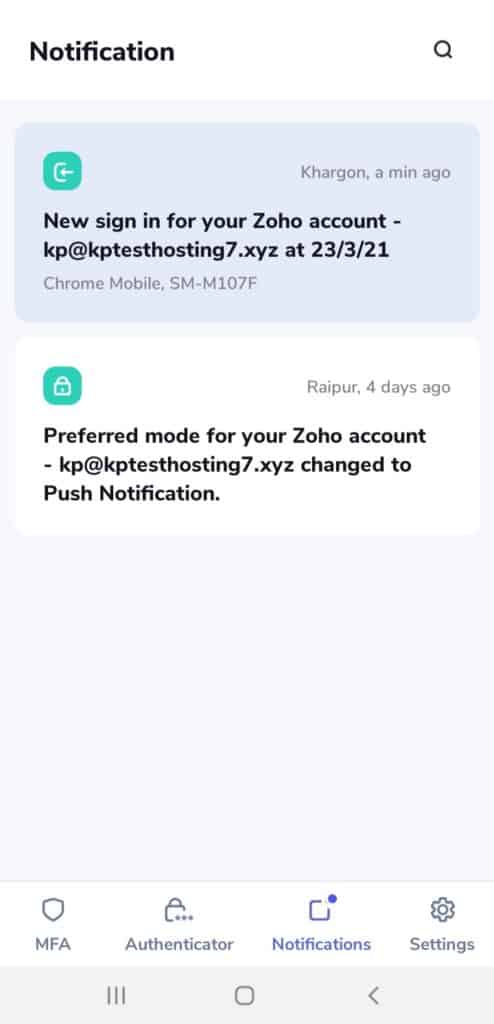
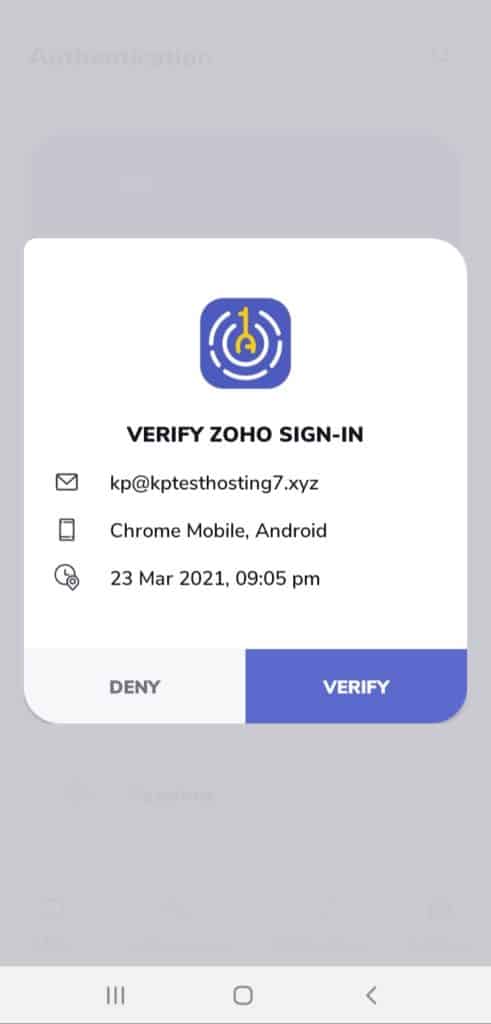
If the Push Notification feature is enabled, it provides you an extra layer of security while logging in to your account through other devices.
Every time a login attempt is made on your account, you receive a push notification within the app that you can accept or deny.
This notification displays the device type, date, and the time of login attempt.
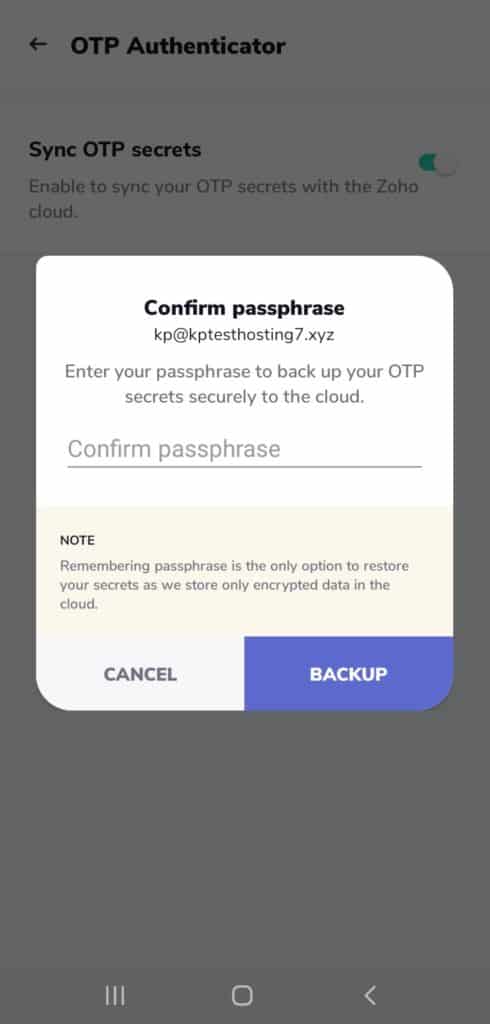
Sync Feature
To enable sync features, you need to sign in with your Zoho account and set up a secure passphrase.
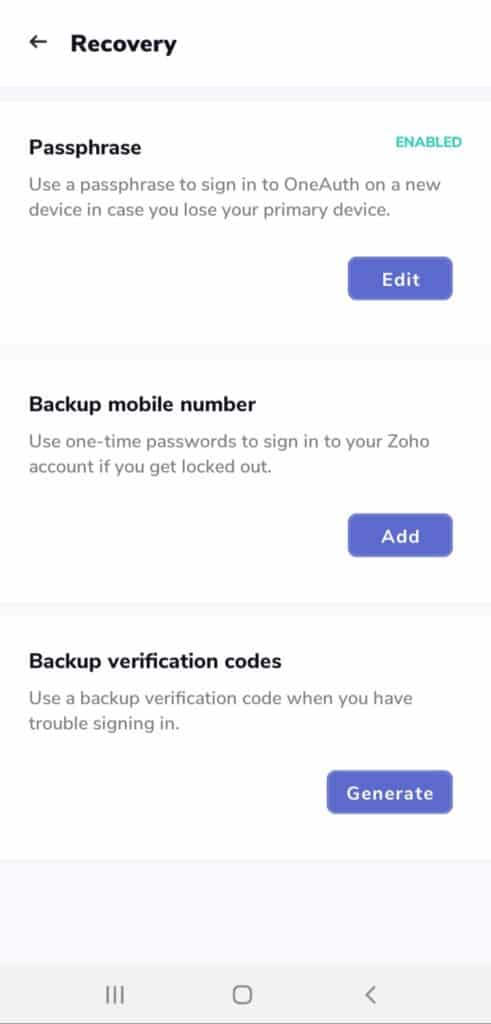
Good Recovery Options
In case you lose your mobile or switch to a new one, Zoho OneAuth app provides multiple options to recover your account.
You can
- Set a Passphrase and sign in to the app on a new device
- Set a backup mobile number to receive SMS OTPs for logging in.
- Use backup verification codes when there is trouble with signing in.
Disadvantages
Needs Internet Connection
Not all the features of Zoho OneAuth work offline. You would require an internet connection if you wish to add a Zoho account, add MFA functions, create backups, etc.
Conclusion
So, Zoho OneAuth is a security-first software packed with loads of features to track, manage, and authenticate your online activities in multiple ways.
And though the basic functions work offline, you need an Internet connection to enjoy all the advanced functions offered by Zoho OneAuth.
Conclusion
So, here’s a quick summary of what we covered in this article:
- What is 2FA?
- Why is it important for you?
- Popular types of 2FA
- How to use a 2FA app?
- Factors for choosing the perfect 2FA app
- The 9 Best 2FA Apps that you can use in 2024
I hope that this article helped you understand the importance of online security and how an authenticator app can help you achieve that!
Are you planning to try out any of the Authenticator apps discussed above? Which apps have you used for securing your accounts?
I’m using Authy for my accounts. Let me know which one are you using in the comments section below!
If you enjoyed reading this review article, and are interested in getting updates on more similar content, then don’t forget to subscribe to my Newsletter!
This is Kripesh signing off! Cheers and take care. I’ll see you guys in the next article! 🙂
FAQ
1.Where are 2FA Backups stored?
Well, it depends on which authenticator app you are using.
Some apps store your 2FA backups on their cloud servers.
For example: Authy, Zoho OneAuth, Microsoft Authenticator.
Other services let you store your backup codes on Google Drive or iCloud.
2. How do you transfer 2FA accounts to a new smartphone?
Most 2FA applications create backups of your accounts and store them on their servers, or let you choose a cloud storage service like Google Drive or iCloud.
So, if you switch to a new phone, you can restore all your accounts.
Some services also allow you to securely export all your entries and then import them on other apps.
3. How do authenticator apps work?
Once you enable 2FA for any website, this happens.
The website provides a secret key (a string of random numbers and letters) which you can enter on your app or scan through a QR code.
While logging into your account, your authenticator app generates a unique 6-digit code by combining the time and the secret key.
The same process is performed by the website’s servers as well.
If both the codes match under the time interval of 30 seconds, then you can login to the website.
4. What to choose: SMS, App, or YubiKey?
The OTPs sent through text messages are the least secure because they can be accessed by hacking the mobile carrier.
Application based 2FA is more secure because it is harder for hackers to gain physical access to your mobile phone. But it is still vulnerable to cyber attacks!
Hardware based 2FA is the most secure form of authentication because it is not dependent on any software, and hackers would require physical access to your Yubikey in order to get the generated code!
5. Is Authy Better Than Google Authenticator?
Definitely! While Google Authenticator seems very convenient, easy to use and supports a majority of websites, it lags in providing important features.
Authy offers secure cloud backups, desktop apps, multi-device sync functionality, and a Pin/biometrics app-lock for enhanced security.
All these features make Authy a more secure and reliable authenticator app.
6. Can Two-Step Authentication Be Hacked?
Though 2FA is very effective at keeping your accounts protected, it might be vulnerable to hacker attacks too.
Through phishing scams like sending you fake warnings of unauthorised access, they can gain access to your OTP codes, and thus bypass 2FA!
7. How do I know which services support 2FA?
Many popular websites support Two Factor Authentication. Check out this article for more information on how to set up 2FA on major websites like Facebook, Google, Dropbox, Twitter, etc.
8. Which services should I protect first?
Ideally, you should first implement 2FA on those websites and apps that contain your sensitive information.
For example: Email accounts, Password Managers, Social Media accounts, etc.
9. Why is 2FA important?
2FA is important in the present scenario because:
It adds a second layer of security to your accounts
It verifies your identity
It protects you from data loss, thefts, and other cyber crimes.
10. Is 2FA really secure?
Email, SMS, and voice-based 2FA are vulnerable to hacker attacks because they can be intercepted.
However, TOTP based 2FA is comparatively more secure because it generates codes on your device that are only valid for 30 seconds! This minimizes the risk of cyber attacks to a great degree.




Amazing resource.
I wish a few of these were iPhone compatible!
Two questions…
1. What do you think of this authenticator https://2fas.com/?
I emailed them to see if they are open source.
2. Would you consider providing a One-Page Summary, like an Excel Spreadsheet, with checkmarks showing the key features of each?
Idea…
I think you could turn a One-Page Summary into a lead magnet that people would gladly give their email addresses for. Plus you could update it every year.
Thanks again for this educational and helpful resource.
Best,
Mary
Excellent article Kripesh!
I Used to use Authy until my backup password failed when I got a new device WITH THE SAME NUMBER. It would not let me use my new device even though I had it set up for multiple devices! In order to recover my account I was asked to delete the app on all devices and reset. That would have been fine with me until…..they came under Twilio control. All Authy userS must now set up an account with Twilio who wants to know what you are SPECIFICALLY using the app for or they will suspend your account like they did mine. What I am using the app for is none of their business. They persist on sending me emails asking me for specific answers to multiple question about my use with the app and for this reason I believe the app is compromised and I would warn all users against it!
Thanks for sharing your experience.
Wrong choice of first place for 2024, Kripesh.
Authy was stopping its multi-platform support as you wrote and has ended the life of the desktop app 6 days ago
https://support.authy.com/hc/en-us/articles/17592416719003-Authy-for-Desktop-End-of-Life-EOL-
They explain clearly that they only want to support what gets them more money. Between this and its being proprietary closed source, Authy is now trash, and you trust your data to a company that offers no way to retrieve them and could shut down any moment. The only reason Authy is still popular is the advertising, and the fact that people are gullible.
Please reconsider your recommendation.
Thanks for pointing this out.
Which one do you think is the best out there?